Privacy-Preserving Machine Learning for Industries
Transportation, Mining and Metallurgy
Functional Transformation (Veils)
image, video
YOLOv7, YOLOv8
Computer Vision for detection of:

Three major companies from the Transportation, Mining, and Metallurgy sectors. Large infrastructure firms manage a vast network of buildings, facilities, and structures distributed across the globe.
Their employees perform daily tasks related to the technical maintenance of these facilities and the communication systems connecting them.
The companies' objective is to monitor the execution and quality of these tasks, as well as ensure compliance with safety regulations. The geographic dispersion of the facilities further complicates this task.
Regularly engaging in R&D and the implementation of machine learning
Exploring the use of third-party cloud platforms for these purposes
Intending to involve external teams of ML specialists
Relying on their own remote specialists
Data related to the use of tools in the production chain and compliance with safety regulations is classified by Customers as sensitive. This is because the video footage captures employees, facilities, and objects, as well as incidents that require thorough investigation.
To efficiently work with ML algorithms, it is essential to involve external specialists, utilize powerful computational resources offered by cloud providers, and grant access to data for employees working outside the clients' security perimeter.

The data owner transforms it into a non-interpretable form using a one-way transformation function

Transfer of non-
interpretable data to
the ML team

Storage of non-
interpretable data

Training an ML model
on non-interpretable
data

ML-model
quality check

Protection of data
sent to the inference
To address the outlined challenges, the Veils method, which belongs to the class of functional transformation methods, was applied.
For the purpose of publicly demonstrating the aggregated results of three different clients, we used the open dataset "Mechanical tools-10000" with five detectable classes. ML experiment tracking was conducted in TensorBoard.
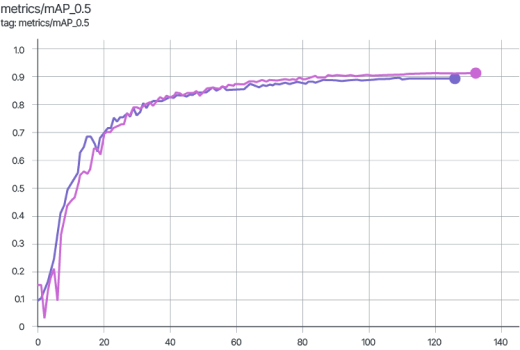
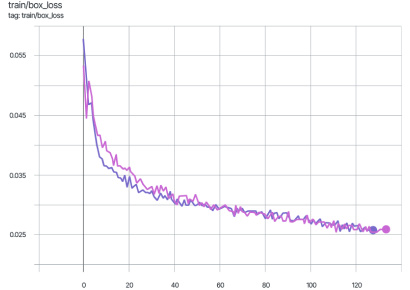
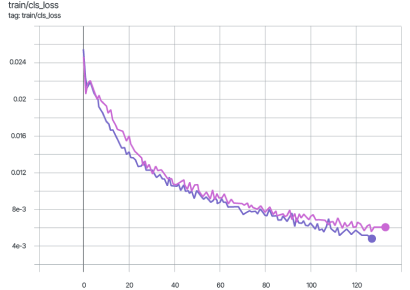
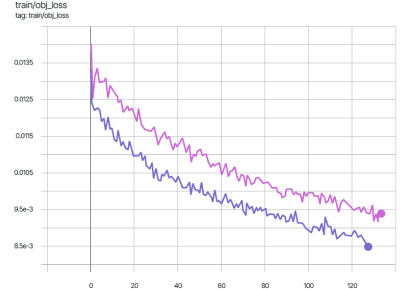
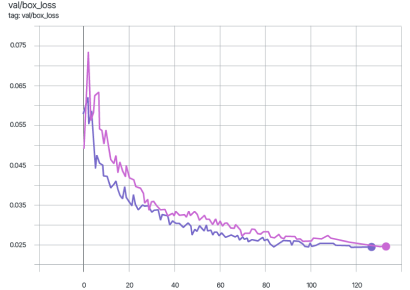
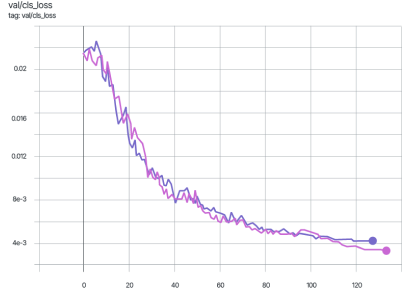
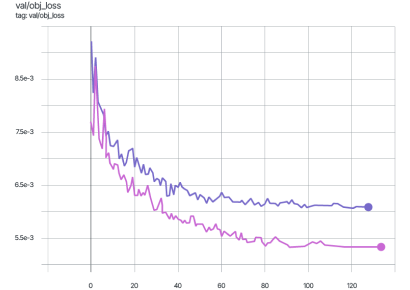
The graphs below display the mAP_0.5 metric during the training of the YOLOv7 model. The pink graph represents training on the original dataset images, while the violet graph corresponds to training on data protected using the Veils method.
As shown in the graphs, the difference in the mAP_0.5 metric does not exceed two percent.
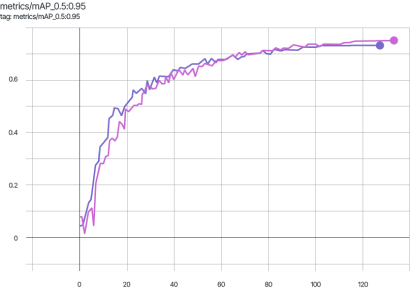
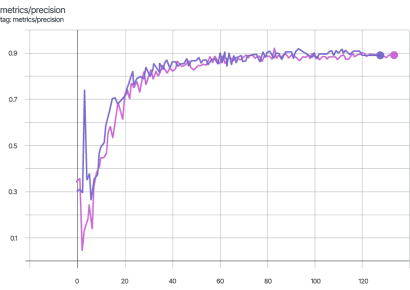
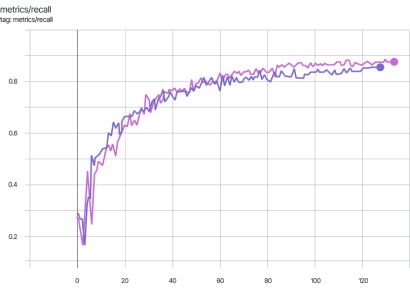
The graphs for other metrics also show similar behavior.









| Input data | Batch size | Epochs | Workers | Max mAP_0.5 | Max mAP_0.5:0.95 |
Run time (hours) |
Dataset size |
|---|---|---|---|---|---|---|---|
| Original images |
10 | 100 | 8 | 0,9082 | 0,7307 | 6 | 332 MB |
| Veils | 10 | 100 | 8 | 0,8917 | 0,717 | 7,2 | 53000 MB |
The computation time of protected data for the entire dataset was 20 minutes on a PC with a GPU and 70 minutes on a PC without a GPU.
Below are the results of applying the trained models to the test dataset of images.
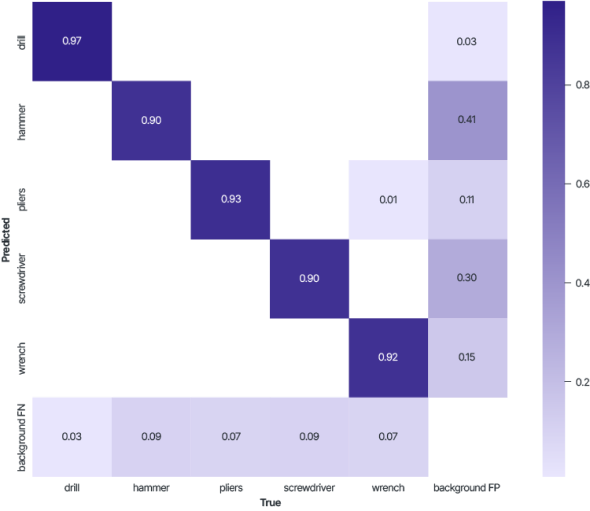
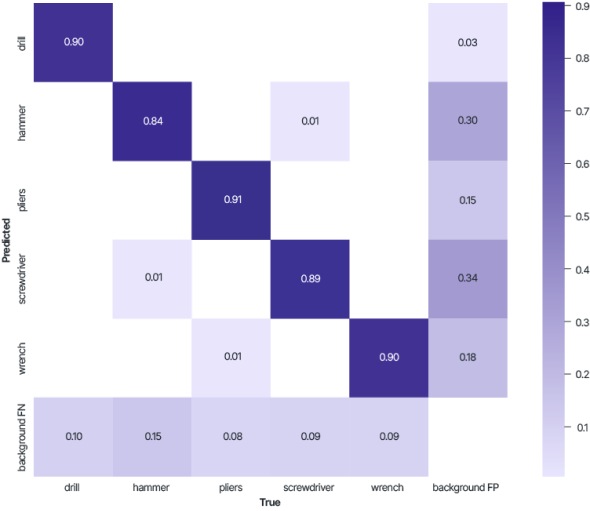
During training, the difference in mAP_0.5 does not exceed 2%.
Results on the test data show that the Veils method, which belongs to the class of functional transformation methods, can be industrially applicable.
The outcome of the projects for clients was the development of ML models trained on protected data for detecting required objects in images.
The solution ensures the subsequent safe transfer of confidential data. This data, collected from numerous distributed video recording points of Customers employees' actions, is sent to local data centers where protected inference is performed on the trained ML model.
This, in turn, allows for monitoring the fact and duration of infrastructure maintenance tasks, as well as compliance with safety regulations.
It also reduces costs for monitoring line personnel, optimizes production processes, and decreases accidents and workplace injuries.
Clients received quantitative data for a more justified employee motivation and reward system and for more favorable negotiations with insurance companies.
The models, as a result of intellectual work, have been protected.

[1] Computer Vision for Safety Management in the Steel Industry
[2] Applications of Machine Learning and Computer Vision in Industry 4.0
[3] Role of Computer Vision in Industry 4.0: Top 5 Use Cases Transforming Manufacturing Industry
[4] Complete Guide to AI-Powered Workplace Safety in Manufacturing
[5] Computer Vision in Workplace Safety
[6] Role of Computer Vision (CV) in Manufacturing
[7] Leveraging computer vision towards high-efficiency autonomous industrial facilities